A rehearsal in staying with painful technologies and a response-in-progress
Key terms of tech trouble
Cutting-edge surveillance, unverifiable tech, high-risk laboratory, ad-hoc-tech that leads to risky security
Abstract
How to do a close reading and unlearning at the same time?
When engaging with trouble that moves with technology.
Especially when sharing space and time is limited.
When complexities and large-scale absorb.
When keeping a sense of personal agency is hardened by abstract realities.

Introduction
This is the beginning of a series about crossed out and crossed over spaces, where I’ll juxtapose unrelated tech situations while activating queer*tech proposals to do otherwise, mostly implicit activations. More of a responding than a referencing. Running threads in parallel until they might come together and I wonder if it‘s possible to get closer while keeping up an oscillation.
I record along with my instrument from the electrosmog of computation.
[ Track 1: smart feature phone in idle state, minutes 0-10]
Log
…………………………………………………………………………….
In response
I had forwarded the call for this blog series to Goldjian, with whom I am in an asynchronous tele-exchange. We got introduced in 2013 by a shared acquaintance. We were both working artistically with operating systems then, as structures that give and take, through sonic and somatic expressions. When we met for the first time, we were four persons with very different practices and backgrounds and looking for other ways of being with computation and each other. We came from choreography, computation, sociology and art and we were doing dance, commandline poetry, video performance and noise. We spend two weeks together to get to know each other and set up a performance. Along the way, we showed the sketchy configuration twice, once at the outdoor, large-scale hacker festival OHM (Observe. Hack. Make.) and the other time at HS63, a small listening venue in Brussels. The first one was a complete disaster, and it took us days to recover. Maybe, this intense point of departure is one of the reasons our exchange is ongoing.
……………………………………………………………………………
Two situations
I’ll have a closer look at two computational situations that have nothing to do with each other. I came across them recently while collecting technological experiments; one is conducted in the lab, and the other one ‘in the field’ or ‘in the wild’, which refers to ‘in real life’. Both are dealing with potential dangers and potential securities.
……………………………………………………………………………
Binary Coal
When I send Goldjian the call, they reacted to the quote by Gumbs about unlearning and pointed me to the experiential oracle [Binary Coal]. The oracle offers a ‘non-binary space for processing the complexity of this moment when blackness operates digitally both as a resource and as a circumscribed and violable form of being’.
The oracle does the split of staying with what‘s wrong in order to overcome it. So I followed the invitation while thinking about oppression through technology and that it targets unequally:
1. ‘What is the most pressing challenge or breakthrough that you are facing in this moment related to blackness, matter, and being you?’
How can I move with others within (sonic) technologies that are violent?
2. ‘Choose a letter of the alphabet that you associate with that question.’
Sonic Technologies
3. ‘Look for the poem or word associated with that letter and read the poem aloud.’
Letter S
spoken
sound
speaking
some
singing
sun
stapled
sign
stub
some
sun
seeking
sparrows
shell
some
#silenceintolanguageandaction
Letter T
total
the
there
the
then
there
teary
the
tooth
threat
tongue
to
through
the
the
take
the
#thetools
I keep a paper with the S- and the T-poem next to my computer.
……………………………………………………………………………
In the lab
A recently published paper titled ‘Hey Alexa what did I just type’ [2] is one of the publications showing the vulnerabilities of smart speakers at home. This one is a bit peculiar as it does not aim at snooping on conversation, but on subtle sounds made by tapping on the screen of another device such as a smartphone. The test setup shows that it is possible to distinguish the sound of different characters and guess a pin or other short data by listening.
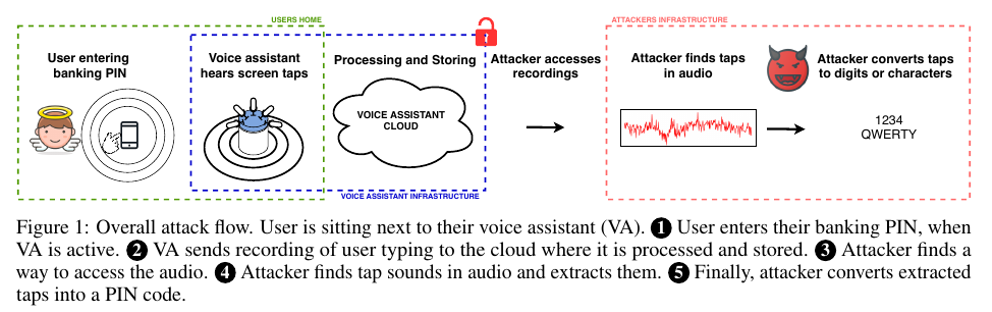
One of the formal conditions of running the experiment was to gather data for 30 minutes per dataset. In the ‘future directions’ section they propose to re-run the experiment with a software radio. It is common for correlations to occur between different physical emissions of a digital device, such as between acoustic and electromagnetic or electric ones.
I do my first recording of the phone.
……………………………………………………………………………
At the border
During 2016-2019, the multiple billions heavy EU project iBorderCtrl [3][4] investigated migration control technology at the border. It involved 13 private or commercial ‘key players in the field’ to grant ‘technological state-of-the-art’. Civil liberty activists claimed to release internal documents [5], partly due to the public funding of the project and partly due to the vague scientific base of one of the components that is relying on AI to detect falsehood from facial micro-gestures and received some of them.
The other biometrical component of the envisioned ‘holistic solution to assist the Boarder Guards’ is a ‘Hidden Humans Detection (HDD)’ device. I looked into one of the technical specifications [6], one of the few documents disclosed until today, whether non-visual procedures were considered.
[ Track 2: smart feature phone in idle state, minutes 10-20]
……………………………………………………………………………
What they have in common is a kind of ignorance-by-design, an ignorance of ignorance.
Goldjian called it ‘dissociation-in-design* where dissociation comes from Somatic Experiencing and refers to a quick shift toward numbness or disconnexion in reaction to an overwhelming painful or disgusting situation, which is similar but flipped to a state of total absorption. In both cases, the responses are immediate, almost automatic, driven by fear, fight, flight responses and little to no space for choice, thoughts, feelings, values or even awareness of what is going on. Or disconnexion-in-design*, such as in value-in-design with the design of technologies being driven by absence, dissociation, ignorance, disconnexion (what Hannah Arendt may call the banality of evil).’
…………………………………………………………………………… ‘You can reassure Julia we have plenty technology; technology is the brilliance of making something out of anything, of making what we need out of what we had’ [Evidence by Gumbs]
The cyberphysical situatedness
The lab setup [2] ignores all societal implications of an ‘afterwards’ once an abuse actually happened and focuses on technical and physical entanglements, how to circumvent them and how to countermeasure the circumventions. Despite the apparent remoteness to social conditions and not even posing a realistic or far-reaching threat, I find a distinct approach in the test arrangement.
Within the various technical knowledge domains, cyberphysical security is the one that might come closest to being ‘situated knowledge’ and recognising it. Concrete physics drives the experimental setups and how the logical procedures show in physical expressions. The interplay of components designed independently of each other is in the centre, as is the embeddedness of a system into its multiple environments.
The experiments or reported hacks dealing with cyberphysical conditions defeat many abstracting and separating practices that constitute informatics and might help think the computational otherwise. They look at what happens to logic once in operation or what might (have) happen(ed).
……………………………………………………………………………‘’ [Evidence]
Setting the scene
The situation at the border [6] sets the scene for abuse, referring to scientific evidence when there is very little witnessing possible of this evidence applied at all, let alone consent or resistance to its putting into practice.
Only introductory, general knowledge, and summaries are in clear text in the few documents handed out by the EU project. The self-affirmations of technological-solution-makers entrusted with solving societal issues is an integral part of it and dehumanising reasoning such as when omitting the ‘person’ from ‘objects or persons’ and referring to ‘target objects’ only.

[ Track 3: smart feature phone in idle state, minutes 20-30]
……………………………………………………………………………‘’ [Evidence]
On the website
This is in stark contrast to the official statements in the F.A.Q. section [7] on their website, that furthermore limit their considerations to persons participating in the pilot study only:
‘How were fundamental rights protected during the testing of the system?
The Consortium, from the beginning of the project, recognized the sensitivity of the proposed approach and technologies from an ethical point of view and took appropriate measures throughout the lifespan of the project, by continuously monitoring and making all the necessary efforts in order to ensure the respect of the fundamental rights of each person directly or indirectly involved. As outlined above, the test pilots were isolated from other proceedings at the border crossing points, whereas they were conducted exclusively using personnel from the iBorderCtrl Consortium; issues with respect to discrimination, human dignity, etc. therefore could not occur for ordinary members of the public.’
The project’s understanding of discrimination and the extent of its responsibility states here:
‘Last but not least, the iBorderCtrl system was seeking to avoid discrimination, by design, whenever possible. This being said, the system included an avatar in both genders and with different languages relevant to the use-cases fostered in the project.’
The assurances are vague (‘human dignity, etc.’, ‘whenever possible’, ‘different languages’) or limited (‘both genders’) and can’t be verified until the processes of the project have been made transparent to the public.
Most strikingly, the project requests an ‘open debate’, while simultaneously fighting with all means to keep relevant information disclosed.
‘Consequently, it is important to accumulate knowledge on the advantages and disadvantages of the technology, and have an open debate on the issues as the basis for an informed democratic decision of society at large. This will help to ensure that such a system will only be used at the border if it provides fairer and better results than the current system, solely relying on human beings.’
……………………………………………………………………………‘’ [Evidence]
‘Bonus: Tweet out the poem you found, the question you asked and any thoughts you had with the hashtag below the letter you chose. And tag @alexispauline and #blackmatteroracle’
I keep surrounding the single words in the S- and the T-poem with quotes from [Evidence] to stay with the trouble.
[ Track 4: typing on a smart feature phone]
About the tracks
Two coils for electromagnetic waves [8] picked up the phone lying on the table. The recordings are almost raw, with some denoising of static noise.
The tracks can be listened to simultaneously.
Activations
[Trouble] Haraway, Donna Jeanne. Staying with the Trouble: Making Kin in the Chthulucene. Experimental Futures: Technological Lives, Scientific Arts, Anthropological Voices. Durham: Duke University Press, 2016.
[Binary Coal] Gumbs, Alexis Pauline. ‘Coal: Black Matter Oracle’. The Black Scholar 47, no. 3 (2017): 3–7.
[Evidence] Gumbs, Alexis Pauline. ‘Evidence’. In Octavia’s Brood, edited by Walidah Imarisha, adrienne maree brown, and Sheree Renee Thomas, 33-42. Oakland, CA: AK Press, 2015.
References
[1] Callamahos, Lambros D. National Security Agency (NSA) Military Cryptanalytics Part III by Lambros D. Callimahos, October 1977, 1977: 437. http://archive.org/details/nsamilitary-cryptalytics-pt-3-1977.
[2] Zarandy, Almos, Ilia Shumailov, and Ross Anderson. ‘Hey Alexa What Did I Just Type? Decoding Smartphone Sounds with a Voice Assistant’. ArXiv:2012.00687 [Cs], 1 December 2020. http://arxiv.org/abs/2012.00687.
[3] ‘Intelligent Portable Border Control System | IBorderCtrl Project | H2020 | CORDIS | European Commission’. https://cordis.europa.eu/project/id/700626.
[4] Project website ‘IBorderCtrl’. https://www.iborderctrl.eu/.
[5] Disclosed internal documents on ‘DocumentCloud’. https://www.documentcloud.org/app?q=project%3Aiborderctrl-41912.
[6] ‘7 D3 1 Data Collection Devices Specifications Redacted – DocumentCloud’. https://www.documentcloud.org/documents/5634636-7-D3-1-Data-Collection-Devices-Specifications: 92-120.
[7] ‘Frequently Asked Questions | IBorderCtrl’. https://www.iborderctrl.eu/Frequently-Asked-Questions.
[8] ‘AC-71/3,5MM’. https://www.monacor.com/products/components/cables-and-plug-in-connectors/adapters/ac-71-3-5mm/
Valentina Vuksic
With a technical and an artistic background, I (she/her) am busy with side-effects of technology and incidental sonic art. My focus is on non-visual technologies and what could be the intrinsic >music< of surveillance society. How technology and its drivers implement >scores< and where surveillance obtains agency. Where >music< and >score< has no predefined meaning with room for improvisation.
Please contact me, if you are interested in any way of research-and-respond about technologies.